In our day-to-day lives, our phones have become an integral part of how we communicate with one another and with the world around us. It is on one device that we store all of our most sensitive, personal, and private information. Being concerned that your iPhone privacy may have been compromised can be a truly awful experience.
However, you need not worry. We’re here to help. There is a possibility that you may have been hacked if something seems abnormal with your iPhone or iPad.
You’re right, that’s correct. It sounds scary, and quite honestly, it is. Your personal details, photos, and videos, as well as your physical location, may be accessible to someone who has hacked your iPhone.
The following guide will explain some iPhone signs that indicate that your iPhone has been hacked. Additionally, you will learn how to improve iPhone security options. It’s likely that your iPhone is hacked if it exhibits any of these symptoms.
Also Read: How to Stop iPhone Screen From Locking Automatically?
Table of contents:
- Is your iPhone hacked? Here are some signs
- If your iPhone has been hacked, what should you do?
- Conclusion
Is your iPhone hacked? Here are some signs
1. You have strange apps installed on your iPhone
On your home screen, swipe left until you reach the screen that says “app library”. Click on the App library and scroll through all your apps.
There’s a good chance your iPhone has been hacked if anything on this list is not something you remember installing.
- Apple’s app store is fairly strict about which apps are allowed. You are more likely to end up with shady apps if you jailbreak your iPhone or download apps from somewhere other than the App store.
- If you share your apple iPhone with another person or are using the family sharing feature. There is a chance that apps you don’t recognize were installed by someone you trust. If you’re worried about unfamiliar apps, ask other members of your family if they’ve installed them.
2. A scary message is popping up on your screen
You might see pop-ups on your phone if it is infected with malware or spyware, but they don’t always mean that your iPhone has been hacked. This is especially true if you see the pop-ups when you aren’t actively browsing the web.
- You will see a pop-up message that says “Your iPhone has been compromised!” while browsing the web. It’s possible that your browser is infected with a trojan virus, but that doesn’t necessarily mean you were really hacked. It’s most likely that you’ll see these pop-ups if you click on a harmful or hacked website.
- Whenever you receive a pop-up message like this, never click on its link or provide any kind of payment. There is no reason why you should have to pay to have your iPhone infected with a virus.
3. In your settings, there are configuration profiles that are unfamiliar
The configuration profile contains settings that can be used to manage email accounts, passwords, and other sensitive information. You may need to install a configuration profile for your work or school so you can access their services remotely. It is also possible for iPhone hackers to trick you into installing profiles that give them access to your phones. You can check iPhone by following these steps:
- You can access your profile and device management by going to your settings and clicking General. You may have been tricked into installing a profile by a hacker if you see any you don’t recognize.
- In case you don’t see this section in your settings, don’t panic. There are no configuration profiles installed, so it means you don’t have any.
4. You are receiving messages that you did not send to your contacts
Hackers may use your iPhone or Apple ID to contact your friends, family, and even strangers if they have control of your device. Make sure no one is sending you messages and pretending to be you by checking your messages inbox and even your mail outbox.
- When you sign into another Apple device with the same Apple ID you use on this iPhone iOS, such as your family mac, your partner’s iPad, or your child’s iPhone. Using your ID, you can view their calls and texts. Before you assume that your iPhone has been hacked, ask your family members whether the calls or messages have been made by them.
- It would be best if you contacted your provider and asked for help in recovering your account in this instance.
5. The amount of data you use has increased
Have you suddenly reached your data or calling limits even though you haven’t done anything differently? Are your phone bills showing strange charges? There is a possibility that something is taking advantage of the mobile data you are sending or receiving.
- Go to your settings app and select Cellular or Mobile. See which apps are using a lot of data by scrolling down to the “cellular data or mobile data” section. You should be cautious if you see anything you don’t recognize.
6. The battery is draining quickly
To access the battery, open the settings app. How much battery power does your phone use? You might find an app that you don’t use often or that you don’t know about. You’re wasting precious battery power, it might be due to malware or a hacker.
If your iPhone has been hacked, what should you do?
How can you protect yourself if you suspect your iPhone may be hacked?
Do you want to wipe all your data? Have you got a new iPhone? What do you think? Throw it away? Thankfully, nothing that drastic has happened!
It is necessary to be able to check your device once and for all to determine if your iPhone have really been hacked. You can do something about it not only once you know for sure, but also by reading the following article.
1. Take a look at your battery usage
In addition to draining the battery more quickly, a background malware program can also cause other battery-related issues. The iPhone iOS system analyzes how much battery power each app uses on your iPhone. As a result, any malware that is causing the battery drain can be easily traced.
- You need to go to settings, choose the battery option, and wait for iPhone iOS to report battery usage. The battery usage of an app is displayed by default on iOS for the previous 24 hours. To see a report on your battery usage for the last ten days, click on the last 10 days tab.
- You can view an app’s on-screen and background activities by tapping show activity above the first app.
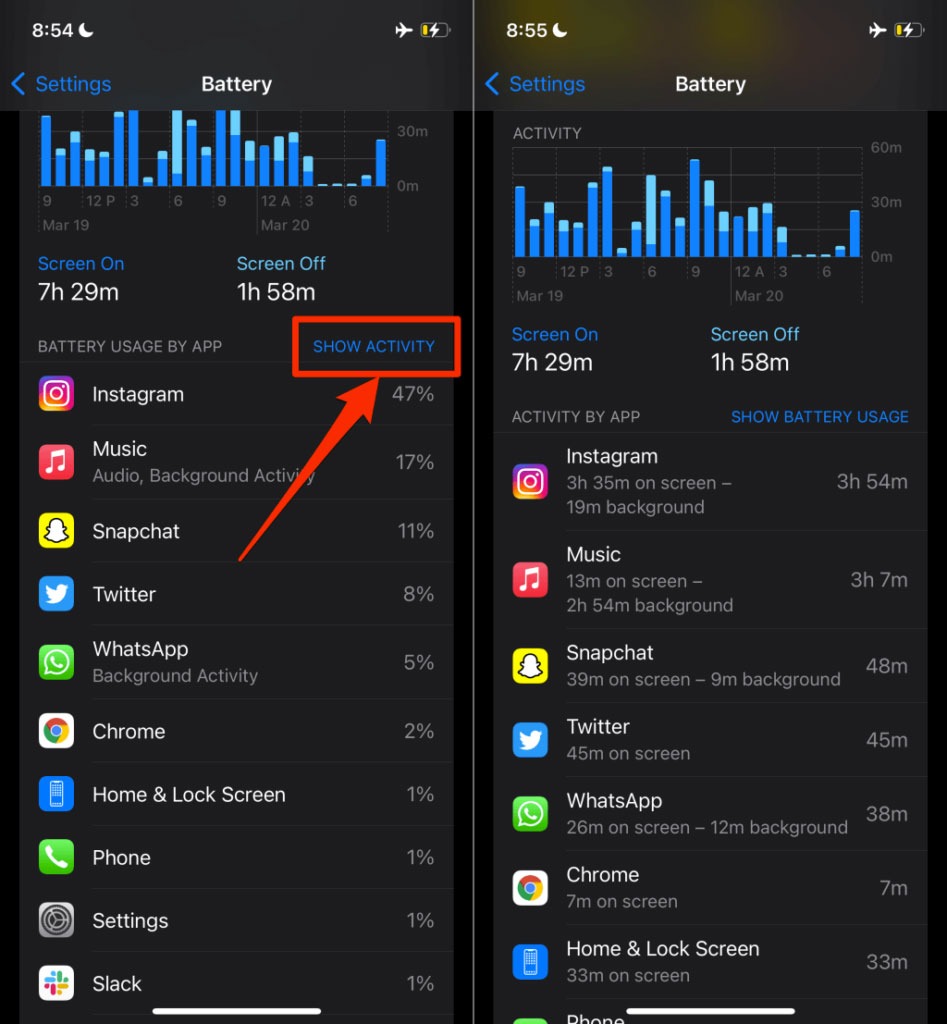
Take a look at your battery usage
Look through the list carefully and note any strange or unrecognized apps that are consuming a lot of battery power and background activity. Check out the next section for more information about what to do if you find out your iPhone has been hacked.
2. Delete suspicious apps
You should remove any iPhone app that consumes a large amount of data, uses a lot of battery life, or has a lot of background activity-especially if it’s an app you rarely use.
- You can access iPhone storage by selecting general in the settings option. When the prompt appears, select the app, tap delete the app, and click delete again on the prompt.
- Alternately, long-press the app on the Home screen, choose to remove from the confirmation menu, then select delete.
3. For suspicious apps, disable data usage
There is a lot of malware that runs quietly in the background, sending personal information to iPhone hackers or developers from your device.
It is common for malware activities to be data-intensive. If your iPhone’s data usage spikes or your limited data plan runs out faster than usual, check your iPhone’s data usage for unknown apps.
- Scroll down to the cellular data or mobile data section of settings and click on cellular data or mobile data
The iPhone apps are ranked according to how much data they consume. Monitor your phone’s data usage and behavior after disabling cellular data access for unknown apps.
4. Public WiFi networks should be avoided
It is rare for public Wi-Fi networks to have solid iPhone security systems. Hackers can easily intercept exchanges between users on websites while they’re using the network because of this. It is even possible for iPhone hackers to create fake public WiFi networks that mimic genuine networks.
You should only use public WiFi networks with VPN if you are required to. By joining such networks, hackers will be able to access your personal information, such as credit card numbers and passwords. By masking your IP address and encrypting your data, VPNs ensure the iPhone security of your connection.
5. Reset your iPhone factory settings
If your iPhone continues to exhibit malware-hacking signs, erase it and reset it to factory defaults.
- First, go to the settings, then general, and then choose transfer or reset iPhone, then erase all content and settings. For the next step, you will need to enter your iPhone’s passcode.
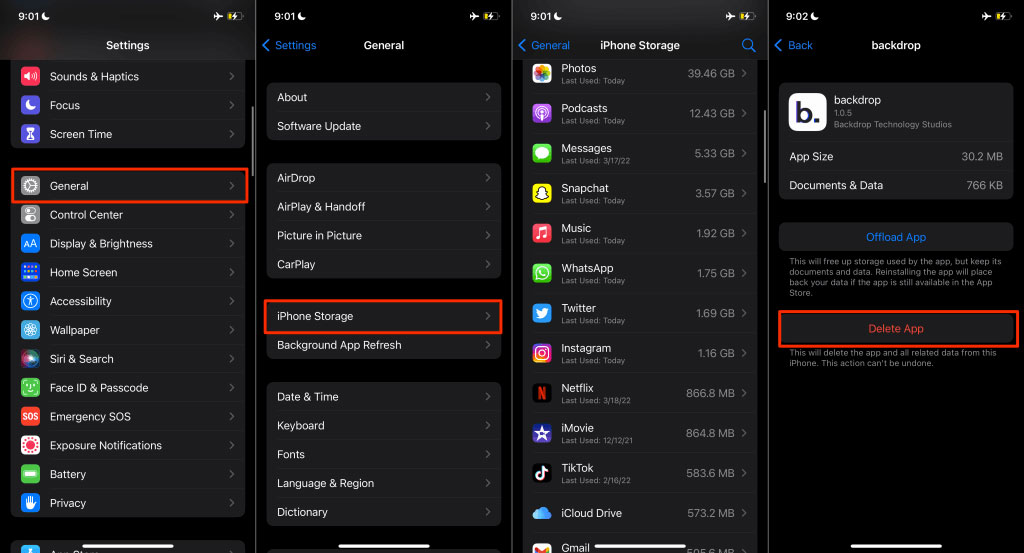
Reset your iPhone factory settings
You can erase all content and settings on iPhone iOS 14 or older by going to settings, general, and then reset.
Conclusion
Almost everyone has experienced getting iPhone hacked at some point in some form or another, and it can be one of the most inconvenient things to happen to someone. The iOS sandboxes applications, which makes spreading malware between apps almost impossible unless you jailbreak your device. The iPhone, however, is not immune from iPhone security threats or hacks. Now you know what to do if your iPhone shows any of the above symptoms. If none of these methods works for you, you can also contact Soldrit for more information. Our company provides iPhone repair services in Bangalore, so we can assist you in any way we can.
Similar Blog: How to Unlock Your iPhone Using Just Your Voice?